SSO Setup - Okta
You will need
- Access to manage Applications within your Okta instance
- A connection identifier, provided to you by your Candu Success Manager
1. Set up Candu as a new Application within Okta
Create SAML Integration
Navigate to your Okta management interface and click Create App Integration.
Replace {CONNECTION_IDENTIFIER} below with one provided to you by Candu.
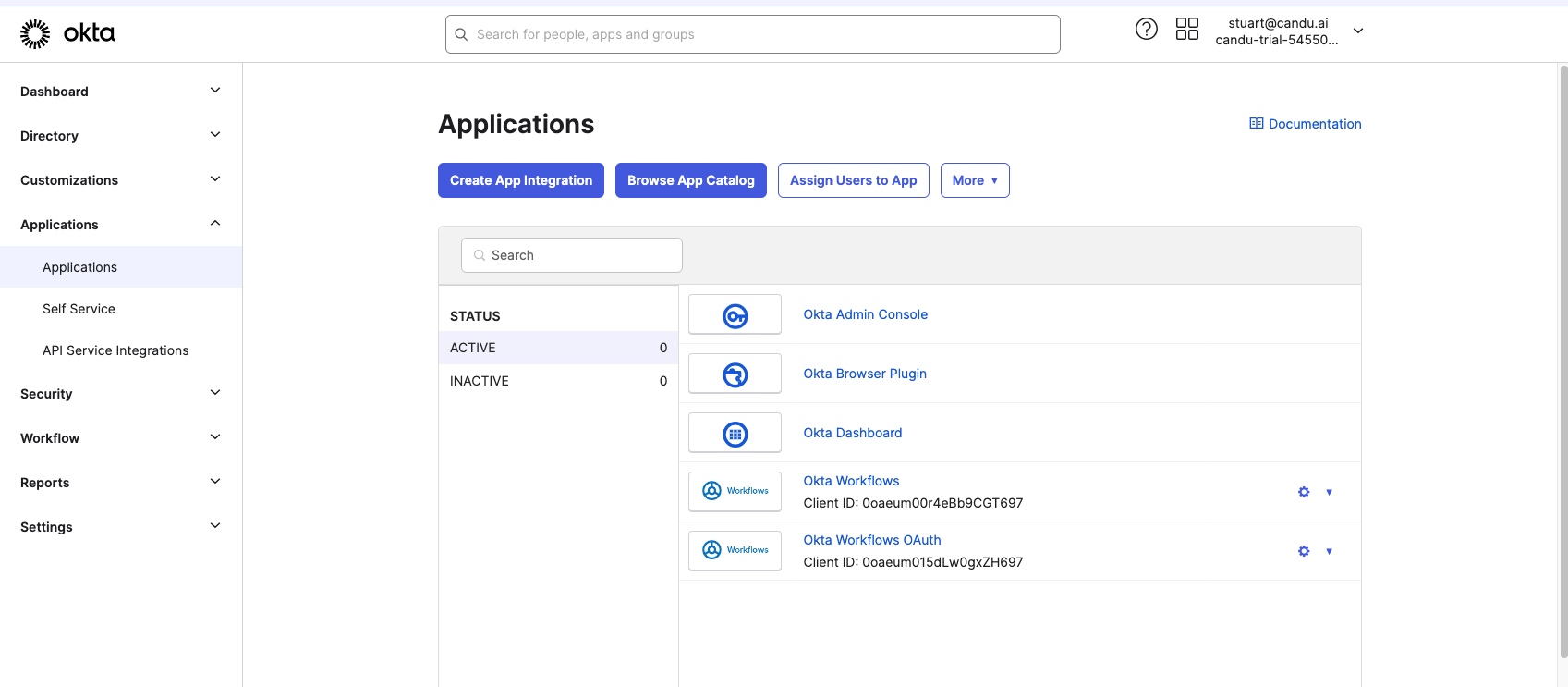
Choose SAML 2.0
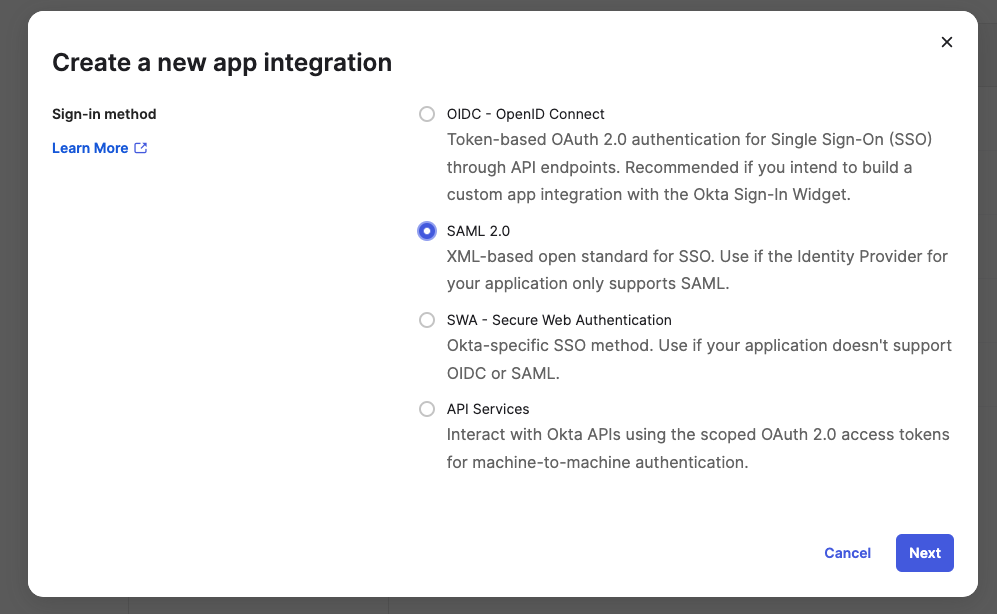
Configure your app name, for example, Candu-SSO, you may want to follow internal naming conventions.
Configure SAML settings
Single sign-on URL:
https://candu.eu.auth0.com/login/callback?connection={CONNECTION_IDENTIFIER}Audience URI:
urn:auth0:candu:{CONNECTION_IDENTIFIER}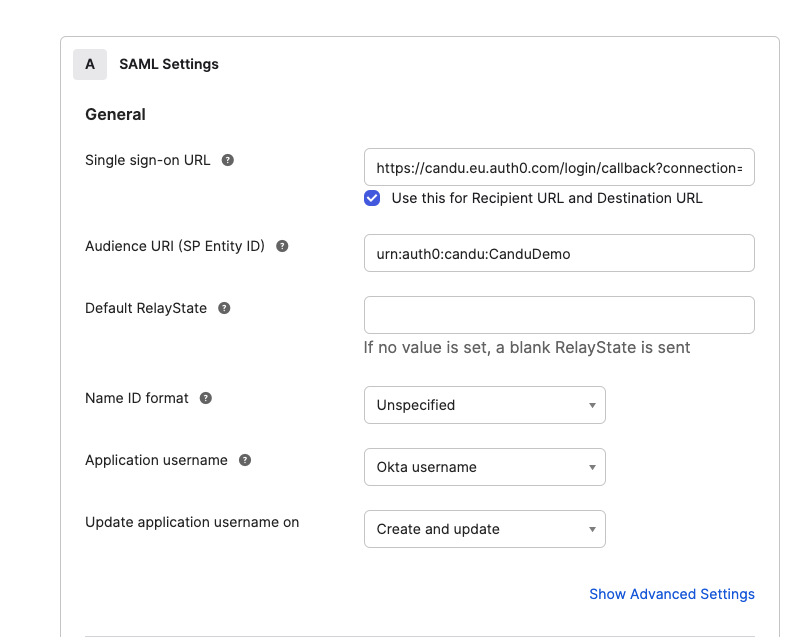
Configure Attribute Statements
Configure mappings for email, name and family_name
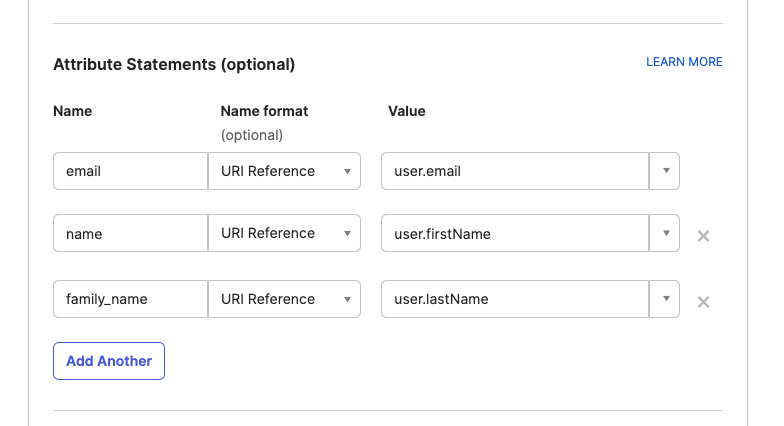
Once these are set you may press next and save the configuration. You can enter feedback survey details if you wish.
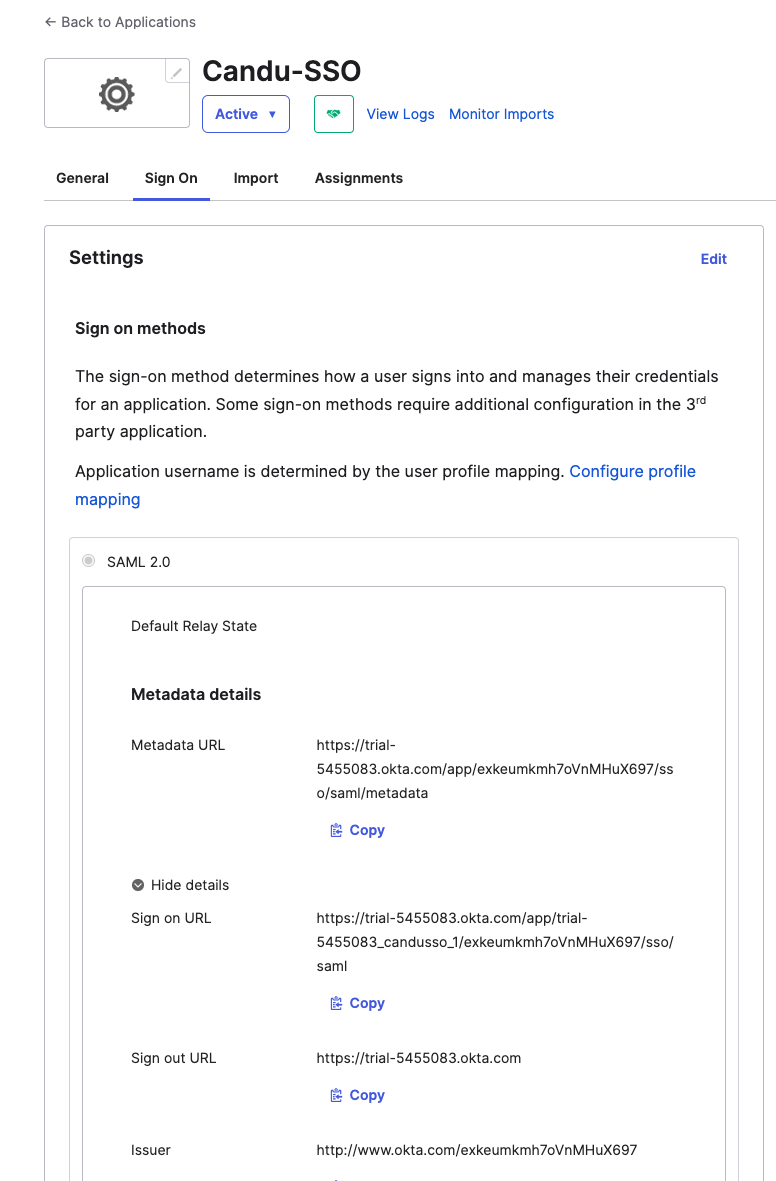
2. Provide Candu with sign in URL & signing details
Please provide us with the following from the "Sign On" section of the configured application:
- Sign on URL
- SAML Signing Certificates - Downloaded from the Sign On section
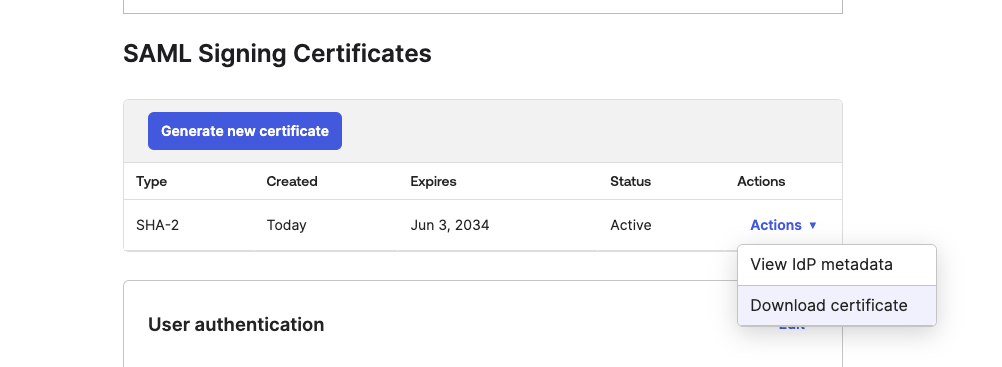
- Sign Request Algorithm - Please confirm the "Type" value from the above. In this case SHA-2
We'll get this set up and then can test the integration ahead of switching over to the singular way to log in.
Note: Mapping user roles
Candu does not currently support mapping user roles. New users will be on boarded as Editors but permissions for those users can be set once they log in.
Existing users signing in with SSO for the first time will retain their roles.
Updated 3 months ago
